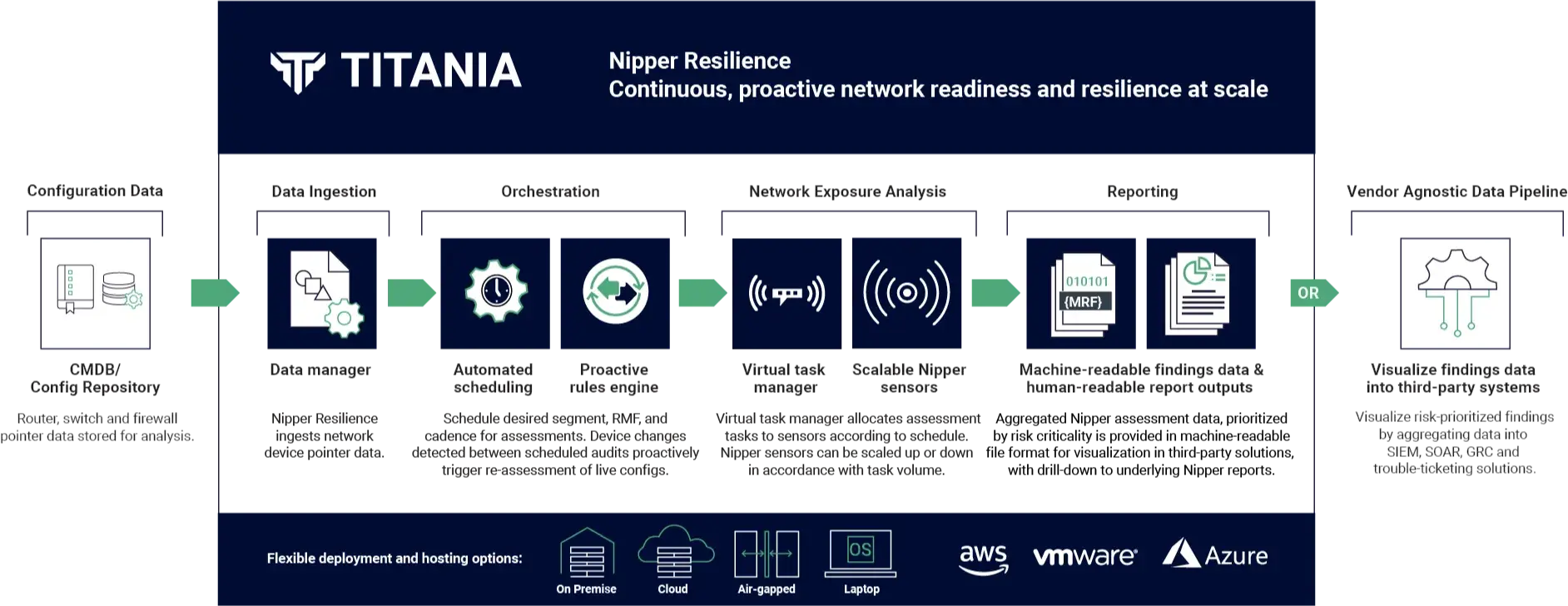
Nipper Resilience for Proactive Network Security
Need ready, recoverable and resilient networks?
Gain real-time visibility and proactive analysis of every network change, to get ahead of threats and accidental networking errors – before they cause operational disruption.
Why networks need Nipper Resilience
Network disruptions – from ransomware, advanced persistent threat groups, accidental misconfigurations or software update failures - can have catastrophic operational, financial and reputational consequences.
Nipper Resilience gives NOC, SOC and Incident Response & Remediation teams the real-time information they need to assure critical networks are ready and resilient to state-sponsored (Volt and Salt Typhoon) and industry-specific attacks, and administrative networking errors; and are quickly recoverable in the event of a disruption or disaster.
The Nipper Resilience solution also provides evidence of compliance with the latest readiness and resilience mandates, including: US GOV Zero Trust, CORA, EU DORA and NIS 2.
Proactively detect, validate and assess impact of every network change to identify exposure and IOCs
Prioritize remediation, response and recovery programs according to business critical disruption impact
Ensure accurate and complete CMDB underpins disaster recovery and business continuity program
Evidence and assure compliance with corporate and/or externally mandated readiness and resilience best practices

Scheduled Network Posture Assessments
Increase the coverage of assessments for up to 250,000+ devices, to improve attack surface management by supporting ZT segmentation and policy enforcement, determining adherence to operational readiness and resilience standards (e.g. CORA and DORA), and automatically reporting pass/fail compliance with:
- PCI DSS 4.0
- NIST
- STIGs
- CIS Benchmarks

Near-Real Time Network Exposure Monitoring
Key to minimizing the attack surface and developing operational resilience, Nipper Resilience proactively monitors all network changes, providing visibility of ZT macro segmentation violations and vulnerabilities, automatically mapped to specific MITRE ATT&CK TTPs and industry specific attack vectors, to:
- Inform scope and focus of threat hunting and incident response
- Prioritize risk remediation by network segment and/or attack exposure criticality
- Determine systematic exploitable vulnerabilities that require a remediation strategy
Nipper Resilience
Architected for the Enterprise
Nipper Resilience has been architected to support internal and external use cases, via multi-tenanted deployments. A horizontally scalable, agentless web-based application, the solution is accessible through modern web browsers. Rest APIs and JSON outputs provide integration with trusted 2FA, CMDB/Git repository, SIEM, SOAR, GRC and trouble-ticketing solutions, to ensure full integration within the proactive security tech stack.
Flexible deployment options include:
- On-premise – deployed on a server; either a physical machine or using a virtualization platform (e.g. VMware ESXi with an Open Virtual Appliance);
- Virtual Private Cloud (VPC) – deployed using an Amazon Machine Image (AMI);
- Flyaway Kit – installed on a physical or virtual laptop
For CMDB-centric Network Resilience
The configuration collection layer within Nipper Resilience can be enacted to auto-populate and maintain the organization’s configuration repository. Enacting the configuration collection layer also provides the additional benefit of allowing users to manage ‘configurations as code’.
Nipper Resilience detects network infrastructure device changes on the target network before securely extracting and storing live device configurations in the provisioned configuration repository. Git-based repositories also allow digital twin environments to be generated, which can be synched with Nipper Resilience to test pre-production configuration changes ahead of deploying them to live devices. Changes made to the live configuration are then proactively re-checked to assure the device maintains a secure state.
Next-Generation Continuous Network Exposure Management Solution
For teams tasked with operational readiness and resilience
- For NOC teams
- For SOC teams
- For Incident Response / Hunt teams
For NOC teams
Up to date CMDBs and near real-time visibility of network changes to:
- Investigate and compare actual, planned and unauthorized network changes
- Manage ‘configuration as code’ to test pre-production config changes, expedite disaster recovery from operational incidents and perform root cause analysis of changes that may have caused the incident
- Assure that ‘tested configuration changes’ when implemented in the live environment have been successful and the device maintains a secure state
For SOC teams
Near real-time visibility of:
- Overall attack surface posture by mission critical segments
- Exposure to APTs’ specific tactics, techniques and procedures (TTPs) as a consequence of network misconfigurations and software vulnerabilities and
- Systematic exploitable vulnerabilities that require a remediation strategy
For Incident Response / Hunt teams
Visibility of:
- Current and historic attack surface postures to inform scope and focus of response and
- Critical indicators of compromise (IOCs) not visible to traffic monitoring solutions
Key Features of Nipper Resilience
Risk Exposure Visualizations
Proactive
Re-assessments
Obscured Segmentation Data
Digital Twin Synching
Customizable Audit Schedules
Configurable Check Parameters
Aggregated Data Analysis
Snapshot
Reporting
Air-gapped Assessments
Complete visibility of Network Change, Exposure and Compliance
Exposure-based:
-
 Segment CriticalityPrioritize exposure risks according to business criticality...
Segment CriticalityPrioritize exposure risks according to business criticality... -
 Attack VectorsView exposure by tactics, techniques and procedures…
Attack VectorsView exposure by tactics, techniques and procedures… -
 KEVsReport exposure to known exploited vulnerabilities…
KEVsReport exposure to known exploited vulnerabilities… -
 Indicators of CompromiseDetect macro segmentation and least privilege IOCs...
Indicators of CompromiseDetect macro segmentation and least privilege IOCs...
Evidence-based:
-
 STIGsAutomate NDM and RTR checks with pass/fail evidence…
STIGsAutomate NDM and RTR checks with pass/fail evidence… -
 NIST SP 800-53Pass/fail evidence of compliance with up to 49 controls…
NIST SP 800-53Pass/fail evidence of compliance with up to 49 controls… -
 PCI DSS 4.0Automate requirement checks for network devices…
PCI DSS 4.0Automate requirement checks for network devices…
Exception-based:
-
 Titania Security AuditDetect where configs deviate from vendor hardening standards...
Titania Security AuditDetect where configs deviate from vendor hardening standards... -
 CISCO PSIRTException-based reports for vulnerabilities…
CISCO PSIRTException-based reports for vulnerabilities… -
 NIST NVDAssess for national vulnerabilities in minutes…
NIST NVDAssess for national vulnerabilities in minutes… -
 CIS BenchmarksCheck for vulnerabilities against the benchmarks…
CIS BenchmarksCheck for vulnerabilities against the benchmarks…
Supported Devices
For specific details on Nipper Resilience's support for vendor’s products, models and versions, please
contact us.









Nipper Resilience Integrations
eyeExtend Connect for Nipper Resilience on Forescout Marketplace
This integration combines Forescout's enterprise-wide device visibility and automated incident response capabilities with Nipper Resilience’s proactive configuration analysis to give NOC and SOC teams near real-time awareness of the impact of every device configuration change on network segmentation and attack surface posture.
ServiceNow CMDB - Nipper Resilience Integration
The Nipper Resilience ServiceNow CMDB app, available within the ServiceNow app store, allows Nipper Resilience users to integrate their ServiceNow CMDB with Nipper Resilience via an authenticated read only API. This allows the solution to sync and provide continuous, passive and proactive security and compliance assessments of networking devices – giving NOC and SOC teams immediate visibility of configuration drift, complete with automated risk analysis of segmentation and configuration data.

Nipper Resilience solution guide: Proactive Network Security
Developing operational readiness and resilience in a rapidly changing threat environment - Your guide to proactive network security with Nipper Resilience.

Emerging best practice in the use of proactive security solutions
Research, carried out by Omdia, reveals more than 70% of organizations have increased spending on Proactive Security solutions to improve the attack surface

Proactive security solutions infographic - top three priorities
An infographic which summarises the key report findings, top 3 priorities and the core challenges organizations need to overcome.
Request a Nipper Resilience Demo
- Prevent network disruptions
- Analyze Exposure to Industry-specific TTPs
- Detect potential Indicators of Compromise
- Guide Incident Response and Remediation
- Accelerate Disaster Recovery
- Demonstrate RMF Compliance