Ready, recoverable, resilient networks
Rely on Titania's proactive network security solutions.
At every stage of the organizational resilience journey - NOC, SOC, and Incident Response teams rely on Titania to protect and recover networks from preventable disruptions, and to minimize attack surface exposure to threat actors causing economic and societal harm.

Research Report
More than 70% of organizations are increasing spending on new Proactive Network Security solutions to ‘bridge the gap’ between current vulnerability assessment practices that leave them exposed, and the continuous monitoring needed to get ahead of active threats and develop operational resilience.
Network
Readiness
Analyze every change
Detect and proactively assess all network configuration changes - planned, unplanned and unauthorized - and gain full visibility of anomalies, including potential indicators of compromise.
- Macro-segmentation violations
- Planned change impact
- Administrative networking errors
Network
Recoverability
Minimize operational disruptions
Maintain up-to-date configuration repositories as the ‘source of truth’, for swift rollback and disaster recovery, root cause incident analysis, and pre and post configuration change validation.
- Incident analysis and response
- Digital twin test environments
- CMDB back-up and restore
Network
Resilience
Mitigate network exposure
View your network vulnerability posture through industry-specific attack vectors to understand exposure to active threats and automatically prioritize remediation of your most critical risks first.
- State sponsored attack exposure
- Adversarial TTPs and KEVs
- RMF compliance failures
Flexible deployment to meet your needs
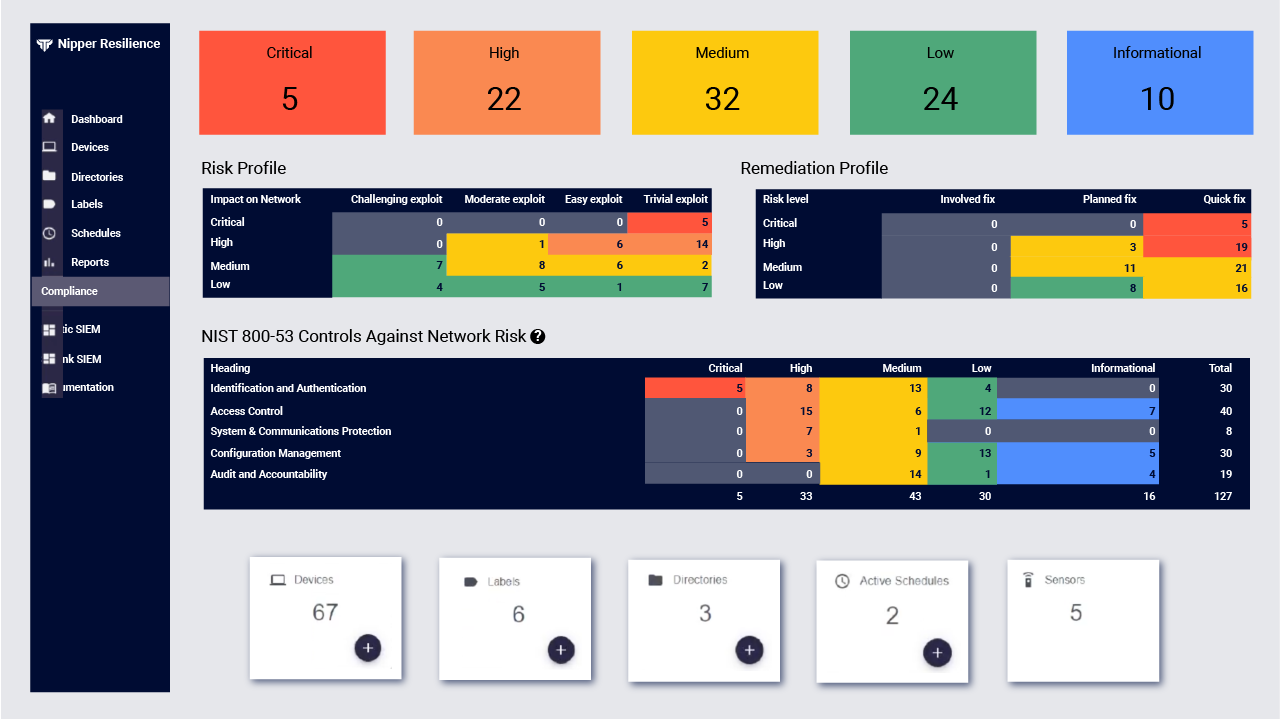
Network Security Posture and Operational Resilience Assurance
Ready to make the shift from risk-based vulnerability management (RBVM) to continuous threat exposure management (CTEM)? It’s time to protect your network from threats and disruptions, with a next-gen solution for NOCs, SOCs, and Incident Response and Remediation teams focused on developing operational resilience.
On-demand Device Vulnerability Assessments
Need accurate network device vulnerability management to compliment your endpoint solution? Determine precisely how routers, switches and firewalls are vulnerable to exploitation – and accelerate the remediation of the most critical non-compliance risks first.
Technical Partnerships










Get ahead of active threats.
Remediate known exploited vulnerabilities.
The impact of exploitable routers, switches and firewalls is global news, as threat actors continue to target these devices to gain footholds in critical networks and escalate attacks. This report investigates why these networks remain vulnerable, and what organizations need to do to get ahead of threats.
Used by cyber leaders focussed on establishing a defendable network.
At the forefront of proactive network security, Titania solutions are trusted by SOC, NOC, Incident Response & Remediation and Cyber Protection teams to safeguard critical infrastructure, their supply chains, and critical commercial entities, globally.

Establishing a defendable network with near real-time configuration change visibility
Elite cyber teams across the US Department of Defense and Fourth Estate complement DISA ACAS with accurate network configuration analysis from Titania.

Maintaining secure and compliant federal networks with readiness and resilience assurance
Helping to deliver on the Executive Order to enhance US national cybersecurity. Teams across 30+ US agencies use Nipper solutions to improve the protection of federal networks.

Preventing attacks and operational disruptions across the education sector
From providing evidence of compliance for defense contracts to protecting student networks from preventable attacks and disruptions, Nipper solutions are used extensively by education institutions.

Protecting the CSP supply chain’s critical networks from preventable disruptions
Telcos and their supply chains choose Nipper solutions to develop greater cyber resilience by managing network exposure that could compromise the vital infrastructure on which industries, governments and societies depend.

Achieving greater security from consistent compliance.
Nipper has long been the choice of auditors that need evidence of compliance with PCI DSS 4.0 is now calling for the continuous security that Nipper Resilience provides.

Improving the security and compliance posture of networks across the energy and utilities sector.
Energy companies have to remediate a large number of misconfigurations detected by OT, so cyber leaders in this space welcome Nipper’s risk-criticality rating to inform remediation workflows.

A Nipper solution for every organization
Internal and external teams use Nipper solutions, with deployments tailored to their use cases, assessment cadence needs, network infrastructure components, and tech stacks. Providing a fast, accurate and complete view of misconfigurations across network infrastructure, Nipper software offers a unique capability for:
Air-gapped Assessments
No need for direct, credentialed device access, enabling CTEM capabilities even in air-gapped environments.
Scalable Architecture
From single devices to network posture assessments for 250,000+ routers, switches and firewalls.
Flexible Deployment
On-premise, on a virtual private cloud with an AMI, as a flyaway kit or as a multi-tenanted deployment.
Enterprise Integrations
With trusted 2FA, CMDBs, Git repositories, SIEM, SOAR, GRC and trouble-ticketing solutions.
Auto-populated Repositories
With a configuration collection layer to maintain Git repositories and manage ‘configurations as code’.
Obfuscated Metadata
Using configuration identifiers for segmentation and metadata labels to protect sensitive device locations.
Customizable Assessments
Configurable Parameters
Find a Trusted Partner
Looking for a reseller, your supply chain partner, or chosen prime contractor? We work with carefully selected channel partners around the globe to ensure Titania software is implemented, integrated, and supported in-country.
Explore Related Resources

The financial impact of exploitable misconfigurations on network security
Find out why there is a disconnect between network security perception and the costly reality, and just how much firewalls are prioritized over switches and routers.

On the radar: Config assessments for security and compliance
“Nipper Resilience adds a level of proactive security risk assessment and vulnerability management, which complements nicely the kind of server-centric vulnerability assessment enabled by the likes of Qualys and Tenable.”

Emerging best practice in the use of proactive security solutions
Research, carried out by Omdia, reveals more than 70% of organizations have increased spending on Proactive Security solutions to improve the attack surface