
Last week, the US Government Accountability Office (GAO) released its findings from a recent review on the efficacy of the Department of Homeland Security’s (DHS) Continuous Diagnostics and Mitigation (CDM) program. GAO concluded that whilst the US government agencies included in the review – the Federal Aviation Administration (FAA), Small Business Administration (SBA) and the Indian Health Service (IHS) – utilized the cyber security tools provided through the program, DHS CDM is still some way off from achieving its goals, and agencies have to do more to optimize the value of their tools.
The CDM program leverages automated tools to assess configurations and identify potential vulnerabilities residing on agency networks. As depicted below, information is aggregated – i.e. comparing the actual state versus desired state – and then displayed on agency and federal dashboards. The GAO report, however, highlighted that the agencies were not “consistently comparing configuration settings on their networks to federal core benchmarks intended to maintain a standard level of security”.
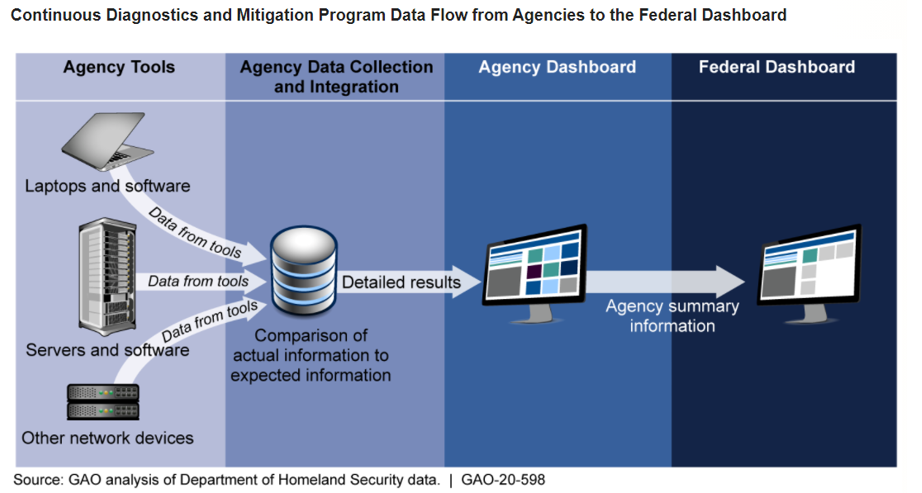
Another issue identified by GAO was the inability of agencies to track when a vulnerability had been remediated, meaning that agencies may not have up-to-date knowledge of their security posture and could waste resources addressing vulnerabilities that have already been remediated.
Users of Titania solutions can assess their performance against benchmarks and controls, such as NIST SP 800-53, related to core network devices to evidence compliance against the CDM Asset Management Capability, and specifically the Configuration Settings Management (CSM) and Vulnerability Management (VUL) capabilities. Titania’s tools can also be used in conjunction with SIEM and SOAR technologies, providing both comprehensive situational awareness of core network device security and playbook-controlled remediation of identified vulnerabilities.
Taking just minutes to set up and generate, Titania’s virtual modelling technology automates line-by-line analysis of device configurations, detecting precise security risks and evidencing compliance with 33 NIST 800-53 controls, in the following control families:
• AC – Access Control
• AU – Audit and Accountability
• CM – Configuration Management
• IA – Identification and Authentication
• RA – Risk Assessment
• CA – Security Assessment and Authorization
• SC – System and Communications Protection
• SI – System and Information Integrity
• SA – System and Services Acquisition
Many of these NIST 800-53 controls can also be mapped to the security practices within the DoD’s Cybersecurity Maturity Model Certification (CMMC) framework, meaning that defense supply chain companies can also automate much of the auditing and track the cyber compliance with the CMMC framework. (For more information on which CMMC security practice checks can be automated with Nipper, and how you can use our software to accurately assess compliance – sign up for our next CMMC webinar
Already in service with all four arms of the DoD, Titania Nipper is trusted to automate the configuration audits of core network devices against DISA STIG and CIS benchmarks to prove compliance with Risk Management Frameworks such as DISA RMF, NIST CSF, NIST 800-53/171 and CMMC. Indeed, Nipper’s proven accuracy advantage is estimated to save the DoD up to 3 hours per device not investigating false positives reported by other compliance tools.
For more information on how Titania can automate CDM compliance assessments for your organization or clients, get in touch.
Matt Malarkey








